Software

Building the Business Case for Improving Endpoint Security
As a security provider, we understand that convincing executives to make changes to their stack can be...

The Gorilla Guide to Achieving IT Asset Management Success
ITAM is about knowing what you've got, where it is, who's using it and how much it costs. If you want...

2021 Data Risk Report - Manufacturing
Our 2021 Manufacturing Data Risk Report focuses on the growing cybersecurity threats facing industrial...

Security Control Guide: Hardened Services Guide
System Hardening is the process of securing a system's configuration and settings to reduce IT vulnerability...

LogRhythm for SWIFT Customer Security Controls Framework
Society for Worldwide Interbank Financial Telecommunication (SWIFT) facilitates a huge number of financial...

eBook: The Business Case for Cloud-based SaaS PLM
Managers comparing PLM solutions need to understand the financial implications of each model. This eBook...

Setting up IT for Success
Every decade or so, we've seen the technology market undergo major shifts. Over the past few decades,...
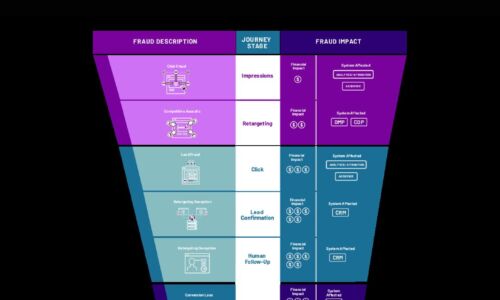
Cybercrime Threatens the Digital Funnel
Cybercriminals are employing new attack methods on new digital surfaces, including digital marketing....

Unified Communications as a Service
As businesses increasingly embrace a cloud-first strategy, many are migrating their most heavily used...

Data Reinvention: Business Transformation Through a New Lens
This HBR Report explores the value that data is bringing to organizations and how to avoid the common...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.



