Software

Zero Trust Access for Dummies
As businesses continue to embrace digital innovation, cloud applications, and the new work-from-anywhere...

5 Critical Requirements for Internal Firewalling in the Data Center
Preventing hackers from hiding inside large volumes of east-west network traffic has now become critical...
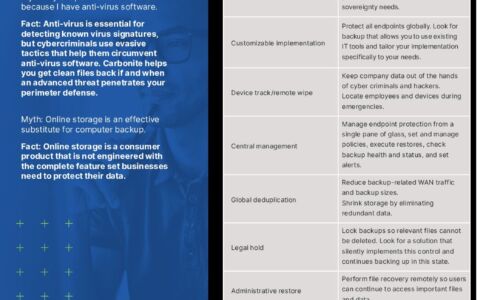
Carbonite Endpoint Protection Myths
Myth: My endpoint data is secure because I have anti-virus software. Myth: Online storage is an effective...

CISO's Guide to Choosing an Automated Security Questionnaire Platform
Failing to adequately screen suppliers' security can lead to data breaches, which can shut down operations,...

Rethinking Insider Risk in the Gig Economy
More and more companies are relying on gig, contract and freelance workers to scale their business. Fully...

Chatbot Starter's Guide
Is your contact center struggling to determine which chatbot solution is right for you? This eBook can...

How 3 Leading Organizations Took the Fast Path to Cloud
VMware Cloud on AWS Case Studies. Whether you are faced with moving specific applications to the cloud,...

2022 Guide to Leading an Agent-Centric Contact Center
Finding and retaining great talent was never easy. But now? Effectively staffing and engaging employees...

Stop hopping on one leg
Go from velocity to value with dynamic DevOps. Don't let old systems and manual processes hobble your...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.




