ERP

Can ZTNA replace your VPN?
Compare 3 remote access approaches Seamless remote access enables companies to boost employee productivity...

EMA Report: Availability and Buying Options in the Emerging SASE Market
Cloudflare One reviewed as a leading provider of Secure Access Service Edge Gartner's Secure Access Service...

MITRE Engenuity™ ATTandCK® Evaluation
MITRE has become the common language of EDR and is the de facto way to evaluate a product's ability to...

The 2022 headless commerce playbook
Is modern headless commerce right for you? Of course, modern headless commerce isn't right for every...

The top 3 IT pains of the new reality and how to solve them
For those considering a better ITSM solution, there are powerful reasons to think beyond just that singular...

Digital Transformation & Risk for dummies
Digital transformation is a critical priority for many companies across most industries, and it's more...

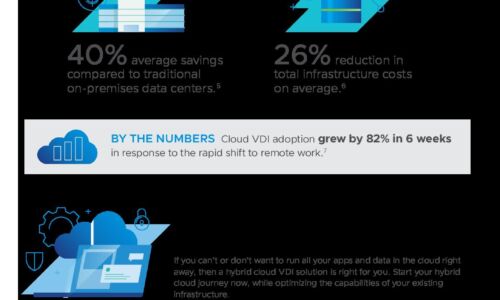
How A Hybrid Cloud Approach Supports Top IT Trends
Today's wave of digital transformation is redefining the role of the CIO, and Gartner surveys chart the...

Human Potential: Unlocked
Find solutions to the problems that matter to you, the CHRO. Managing risk, increasing revenue, boosting...

Forrester Opportunity Snapshot: Zero Trust
Cloudflare commissioned Forrester Consulting to explore the impact of 2020's disruptions on security...
Connect Everywhere: Better Voice Communications for Microsoft Teams
We used to have separate physical devices for phone calls, email and chat, and video conferencing. Over...

Securing applications in the education industry
The role of technology in education has changed radically in the last two years. Like many other areas...

Fast Track to the 5G Edge
As more service providers move toward 5G, they need a scalable, secure, cloud-native infrastructure that...

When Networks Meet The New Tomorrow
This paper looks at IT priorities that organizations will need to address now and in the new tomorrow: +...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.