Data Center

The 10 Biggest and Boldest Insider Threats of 2019 and 2020
That risk is only increasing in an era of remote working and distributed teams. Without a holistic security...

Get Total Endpoint Security with KACE
As an IT professional, you're likely under pressure to manage an increasingly complex environment, while...

Managing Mainframe Phishing Vulnerabilities
Mainframes are undisputedly the most mature, secure and best defended computing platform. Yet even mainframes...

7 Machine Learning Use Cases
Businesses have the opportunity to unlock significant value across the organization with the help of...
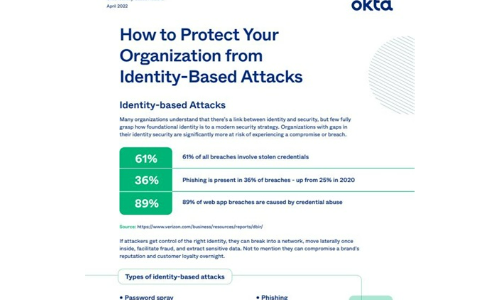
How to Protect Your Organisation from Identity-Based Attacks
Many organizations understand that there's a link between identity and security, but few fully grasp...

Unlock the Power of Hybrid Cloud with Consistent Operations eBook
Embracing a hybrid cloud operating model creates new possibilities for IT organizations, paving the way...

Business Growth and Agility in the Cloud - Infor vs NetSuite
If you want to go further, grow faster and achieve more than your competitors, you need to have the right...

The CIO’s Guide to Data and Analytics Innovation
Discover how Workday enables businesses to make faster, better decisions with one source for all your...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.





