Data Center

IoT Smart Cities & Buildings
Many of today's commercial buildings predate modern energy-saving tools and techniques. That means they...

The Forrester Wave™: Privileged Identity Management
in our 35-criterion evaluation of privileged identity management (PiM) providers, we identified the 11...

Securing Digital Innovation Demands Zero-trust Access
To accelerate business and remain competitive, CIOs are rapidly adopting digital innovation initiatives...

Future Ready with SaaS Management Guide
For today's modern IT organizations, applications are driving both digital transformation and business...
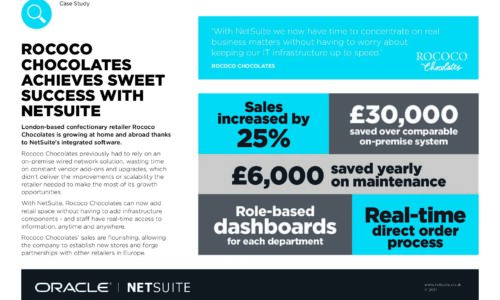
Rococo chocolates achieves sweet success with NetSuite
London-based confectionary retailer Rococo Chocolates is growing at home and abroad thanks to NetSuite's...

The UK 2020 Databerg Report Revisited: Public Sector Edition
This UK Public Sector Databerg report surveyed senior Public Sector decision makers on the data challenges...

Sauce Visual Component Testing
Sauce Visual Component Testing provides organizations the ability to quickly automate the testing of...

The Digital Workspace: Three Elements of Success
IT leaders say they are actively pursuing digital workspace strategies but still need to overcome some...

Delivering On Demand: Momentum Builds Toward Flexible IT
These days, it's well understood that technology has changed the way we manage businesses, serve customers...

Getting started with CASB
Migrating to the cloud can make your business more agile, flexible, and efficient—but it can be risky....

Ransomware Survival Guide
Be Ready for Ransomware Ransomware is an old threat that just won't go away. While overall volumes have...

Dell EMC PowerStore: Data-centric, Intelligent, Adaptable Storage
This report provides a brief introduction to Dell EMC's PowerStore mid-range storage appliance and documents...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

