Authentication & Access Systems

Next-Gen Digital Transformation for Law Firms
Optimize opportunities to grow your practice and mitigate risk. Law firms, like other businesses, have...

20 Examples of Smart Cloud Security
Smart cloud security provides critical capabilities such as governing access and activities in sanctioned...

32 Security Experts on Changing Endpoint Security
For many companies, the modern business environment has become a mobile workplace in which employees...

Top 5 Ways to Simplify Data Protection with Microsoft Azure
Read this white paper to find out five ways that you can simplify data protection with Microsoft Azure,...

The Total Economic Impact™ Of The CB Predictive Security Cloud
Your endpoints are one of the most targeted assets in your organisation. In 2017 alone, more than 50%...

Optimized Security for Multi-Cloud laaS Environments
No question: Multi-cloud adoption can benefit your business. New question: How can you secure multi-cloud...

From Seismic Disruption to a New Era of Success
No one could have foreseen the terrible impact of the COVID-19 outbreak on humankind. In business too,...

The Top 5 Myths of Cloud Security
Hybrid cloud security is a hot topic, especially with the massive growth of public cloud providers like...

Securing Privileged Accounts: Three Steps to Maximize Protection with MFA
Hackers are eyeing your privileged accounts, so you better be using more than 'admin123' to secure them. Multi-factor...

Dissecting a Cloud Attack: Securing Azure with AzLog
Microsoft Azure is one of the fastest-growing cloud infrastructure services. Unfortunately, the advantages...

Why you need an adaptive security segmentation solution
The threat landscape is more dynamic than ever before, and as business-critical applications traverse...
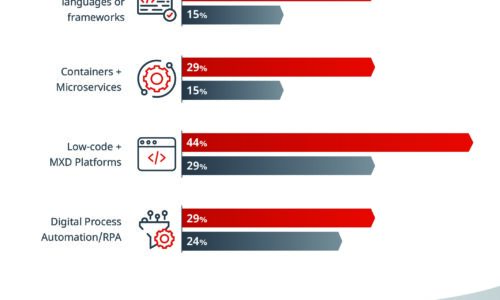
What Separates the Best from the Rest
Some IT organizations have the speed and adaptability to change course quickly when disaster strikes...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

