Applications

NetSuite ERP vs Epicor ERP vs Sage Cloud
Enterprise resource planning ranks high among the most comprehensive, powerful data management solutions...

The US Customer Experience Decision-Makers' Guide 2019-20
The US Customer Experience Decision-Makers' Guide is a major annual report studying the CX strategy,...

The UK 2020 Databerg Report Revisited Executive Summary
Cloud technology hasn't been around for long, but it's evolution in that time has been nothing less than...

eBook: Visibility in Action
Leading companies pride themselves on offering excellent customer experiences based on positive engagement:...

Reimagine How Work Gets Done - Introducing Fujitsu Work Life Shift
It's time to reimagine a new future. The concept of the workplace has changed forever. It's no longer...

Sauce Labs AutonomIQ SaaS App Testing Challenges
SaaS applications like Salesforce or Oracle Cloud need to be tested continuously as they undergo frequent...

Security's Privilege Crisis
Despite spending $114B on cybersecurity in 2018, the onslaught of security breaches continues unabated.1...

Proofpoint Security Awareness Training
Proofpoint Security Awareness Training Enterprise helps you deliver the right training to the right people...

Mobilising employee productivity in the distributed workplace
Citrix and Microsoft shape modern workplaces that unite the essential elements of today's distributed...
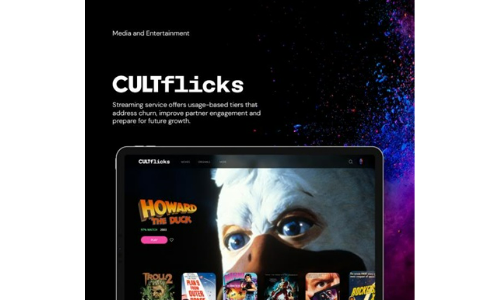
Cultflicks
CULTflicks is a niche video streaming entertainment company that offers the unique experience of specialized...

Addressing the Top 10 Security Issues Organizations Face
Cybersecurity must be a top-level priority for any organization and for many it is. Security should be...

2022 MSP Threat Report
This report was created by the ConnectWise Cyber Research Unit (CRU)—a dedicated team of ConnectWise...
Running Windows on AWS eBook
Migration to the cloud is not merely a journey, it's a major step toward business transformation—and...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.
