Applications

How to Get and Maintain Control of Your Microservices
Learn how a hybrid application delivery system powered by Citrix ADC can help you gain control of your...

HP Proactive Insights Experience Management
Today's work environment looks a lot different than it used to. And it's still evolving. More of us are...

GBS on Now - Make work flow across the silos
Today, there is a need to re-imagine the role of delivery structures within the enterprise. A new global...

Overcome Database Indexing Challenges
Overcome your database indexing challenges – read this MSSQLTips white paper today By properly using...

The CISO's Guide to Ransomware Prevention
Ransomware attacks have transformed the cyber attack landscape. These sophisticated and persistent threats...
GigaOm Radar for Phishing Prevention & Detection
Get your complimentary copy of this independent GigaOm Research report, which analyzes positioning and...
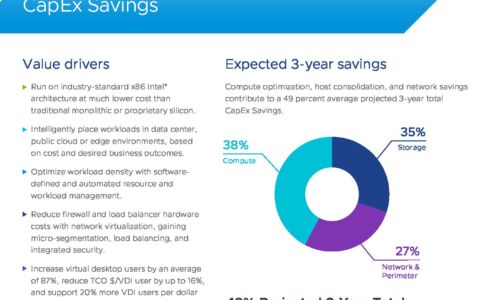
VMware Cloud Foundation: Maximise Digital Business Value
76% of IT organizations are committed to hybrid cloud as a long-term strategy to quickly adapt to changing...

7 Habits of Highly Effective DevSecOps Teams
Security teams are responsible for safeguarding assets in the cloud to maintain compliance and eliminate...

2022 State of Customer Experience Technology
Business and technology leaders at companies large and small, across multiple industries, have identified...

An introduction to eSignature
Stacks of papers that need to be signed, filing cabinets full of paperwork— these are quickly becoming...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.



