Latest Whitepapers

Time to Replace Laser Scanners: Myth-busting Software Scanning
Last mile operations are complex and challenging. Delivery companies across the globe are increasingly...

Analysing the Economic Benefits of Proofpoint Insider Threat Management
Did you know the average annual cost for insider threats is now $11.45M, according to Ponemon Institute?...

Advanced MySQL 8
Design cost-efficient database solutions, scale enterprise operations and reduce overhead business costs...

Data Governance Is Everyone’s Business
Erwin's contribution to data governance brings IT and business together for a new era in data-driven...

Cloud Security Fundamentals
Protecting a cloud environment requires a dedicated, comprehensive effort across the policies, processes,...

Brute Force: Guide to Mitigating Attacks
A brute force attack is when an attacker attempts to gain access to an environment by identifying valid...

Hybrid Work: Why it's time to move your on-premises PBX to the cloud
For years, the shift to cloud-based communications services was gradual, with some organizations going...

OutSystems for Digital Banking
Create a Frictionless Digital Banking Experience With the Power of Low-Code The retail banking industry...

4 Low-Code Best Practices for SAP Fiori Apps
It has been proven that enterprise IT teams that include a no-code/low-code approach for their SAP app...
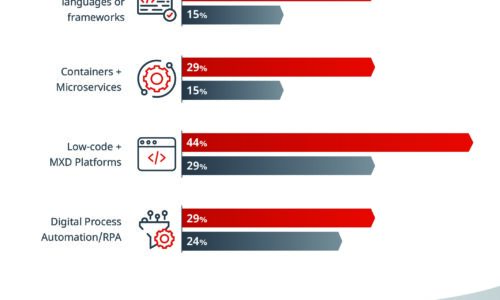
What Separates the Best from the Rest
Some IT organizations have the speed and adaptability to change course quickly when disaster strikes...

Key Steps to Optimizing Cloud Security
Do you know what's missing from your cloud security strategy? There's no question that moving to the...

VMware NSX Advanced Load Balancer Benchmark Report
Moving from appliance-based load balancers to software-defined VMware NSX Advanced Load Balancers could...

2022 MSP Threat Report
This report was created by the ConnectWise Cyber Research Unit (CRU)—a dedicated team of ConnectWise...

5 Reasons to Prioritize Software Security
The pace of digital transformation has reached a speed never before seen, forcing organizations into...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.





