VPN
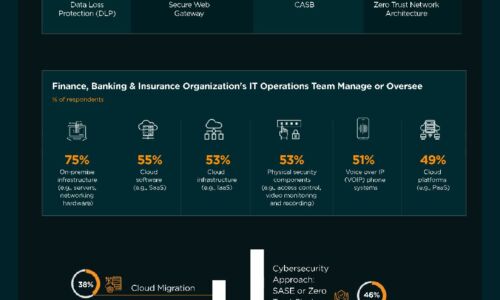
Finance, Banking & Insurance Industry | State of Cybersecurity 2021
This infographic by ISACA and HCL Technologies discusses the state of cybersecurity within the finance,...

The state of industrial security in 2022
Security for the industrial internet of things (IIoT) and operational technology (OT) is in its infancy...

DynamoDB Users-Why Switching to Couchbase Will Save You Time and Money
Businesses using the Amazon Web Services (AWS) cloud often store their data in Amazon's DynamoDB database...

The Pitfalls of SASE Vendor Selection: Features vs. Strategic Outcomes
After speaking with 1000s of IT pros, we've learned that success with SASE is only achieved when it meets...

Don't Diverge—Converge
Digital acceleration is driving the adoption of hybrid IT architectures. These new hybrid environments...

Top 10 Best Practices for vSphere Backups
More and more companies come to understand that server virtualization is the way for modern data safety....

Human Factor Report 2021
Cybersecurity, Ransomware and Email Fraud in a Year that Changed the World As the global pandemic upended...

Enduring from Home: COVID-19’s Impact on Business Security
Faced with shelter-in-place orders in their home counties and states, countless companies transitioned...

20 Examples of Smart Cloud Security
Smart cloud security provides critical capabilities such as governing access and activities in sanctioned...

Implementing the NIST Zero Trust Architecture with Zscaler
The National Institute of Standards and Technology (NIST) has defined the core components of zero trust...

8 Keys to Securing Your Remote Workforce
Modern remote teams are made up of whatever combination of people can get online and get the work done....
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

