SASE
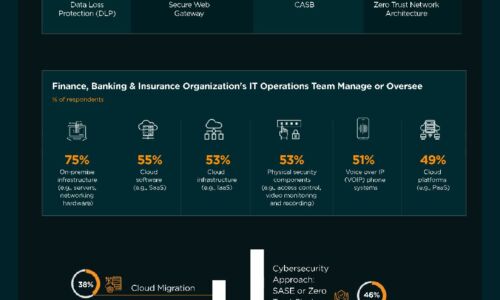
Finance, Banking & Insurance Industry | State of Cybersecurity 2021
This infographic by ISACA and HCL Technologies discusses the state of cybersecurity within the finance,...

The state of industrial security in 2022
Security for the industrial internet of things (IIoT) and operational technology (OT) is in its infancy...

Cloud Data Security 2023 Report by ESG, a division of TechTarget
…More than half (59%) of respondents believe that more than 30% of their organization's sensitive data...

Secure Access Service Edge Palo Alto Networks SASE Comparative Report
This comparative test was commissioned by Palo Alto Networks to evaluate the security efficacy of leading...

3 Reasons to Choose Managed Detection and Response
Cyber threats affect data security in all organizations, but organizations in highly regulated industries...

An Authentication Authority at Your Fingertips: PingFederate
Having an authentication authority within your infrastructure allows you to have a single source of truth...

Network Security Approaches and the Case for Zero Trust
Top executives say that legacy network technical baggage is holding them back from transforming their...

Cybersecurity strategies need to evolve.
Over the past 20 years, cybersecurity strategies have primarily focused on protecting the network perimeter...
Explore your SASE side
Secure Access Service Edge (SASE), is an architecture that ultimately will integrate networking and network...

Office of the CTO Report: Continuous API Sprawl
APIs are a contract between the service provider and service consumer. When any application uses an API,...

An Overview of Cato Data Loss Prevention (DLP)
ata is the most valuable asset a modern enterprise has. The evolving threat landscape and shift to cloud...

Implementing the NIST Zero Trust Architecture with Zscaler
The National Institute of Standards and Technology (NIST) has defined the core components of zero trust...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

