SaaS

The future of IT is now
For technology leaders, the next few years will be feast or famine. The rise of platforms as a service...

Supercharge your digital workspace
Delivering a great user experience is everything. You already know the advantages of secure digital workspaces...

Data Protection Playbook for All-Flash, Cloud-Ready Storage
Learn how to bring unparalleled flexibility and scalability to the way you protect your mission critical...

Building Your Best Boardroom
How to Find the Right Directors For a Complex Future With the advent of modern governance, directors...

All-Flash Buyer's Guide: Tips For Evaluating Solid State Arrays
Are you looking to switch to all-flash storage? Learn how to evaluate your storage options to increase...

How to Achieve Cloud Success with Hybrid Cloud Operations
A hybrid cloud operating model can provide significant benefits for traditional and modernized IT. However,...

Rackspace Openstack Private Cloud
Rackspace® OpenStack® Private Cloud simplifies cloud adoption by delivering a fully managed OpenStack...

Delivering Fast and Secure Enterprise Applications
Adopting a zero trust security model — authenticating and authorizing every request, device, and user...

Advanced MySQL 8
Design cost-efficient database solutions, scale enterprise operations and reduce overhead business costs...

CISO’s Playbook to Cloud Security
To secure enterprise assets in the cloud, CISO's must address several new challenges unseen in traditional...

How to Increase Agility with Hybrid Cloud Automation
As organizations innovate faster than ever, they bring new applications and services to market in more...
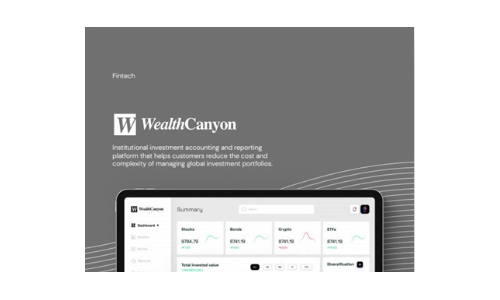
Wealth Canyon
Software companies in the financial industry, such as WealthCanyon, face challenges in collecting and...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

