Open Source

The State of the State of Application Exploits in Security Incidents
Cybersecurity is always about perspective, and that's doubly true when talking about application security....

Networking and Information Systems (NIS) Directive
The NIS Directive has been designed to work alongside data protection legislation. It will be governed...
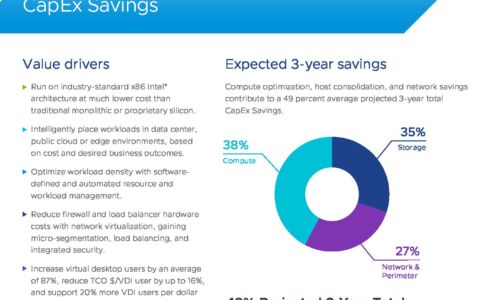
VMware Cloud Foundation: Maximise Digital Business Value
76% of IT organizations are committed to hybrid cloud as a long-term strategy to quickly adapt to changing...

15 Ways Your Website is Under Attack
Web applications are the home of your business on the internet. The functionality within your website,...

Building a Cloud-Native, Hybrid-Multicloud Infrastructure
Today's world is based on the hybrid cloud. Business interactions occur on-premises, through digital...

Security Control Guide: Hardened Services Guide
System Hardening is the process of securing a system's configuration and settings to reduce IT vulnerability...

Raising the Bar for Web Application and API Security Solutions
Securing the web applications and APIs that underpin cloud architectures is a challenge for security...

Modernize application delivery with cloud services
The pace of digital transformation is accelerating as businesses adapt to changing customer expectations....

7 Habits of Highly Effective DevSecOps Teams
Security teams are responsible for safeguarding assets in the cloud to maintain compliance and eliminate...

Seven reasons why your enterprise needs intelligent search
Organizations are hungry to use data to grow and improve performance, but enterprises are struggling...

VMware Multi-Cloud Architecture: Enabling Choice and Flexibility
In today's world, application growth is unprecedented and enterprise applications on a wide range of...

Secure Beyond Breach
Securing the perimeter is no longer enough. The focus has shifted to ensuring your organization continues...

How Do Vulnerabilities Get Into Software?
There isn't a business today that doesn't produce or purchase applications in order to run more efficiently....
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.
