Mobile Security

Rackspace Fanatical Support for AWS
As organizations move their workloads from traditional data centers to AWS, IT security paradigms are...

Next-Gen Digital Transformation for Law Firms
Optimize opportunities to grow your practice and mitigate risk. Law firms, like other businesses, have...

How Malware Can Steal Your Data
As applications drive business, more and more valuable data is accessed and exchanged through them. Cybercriminals...

Understanding the Obstacles to WAN Transformation
Network engineering and operations leaders are looking to software-defined wide area networks (SD-WAN)...
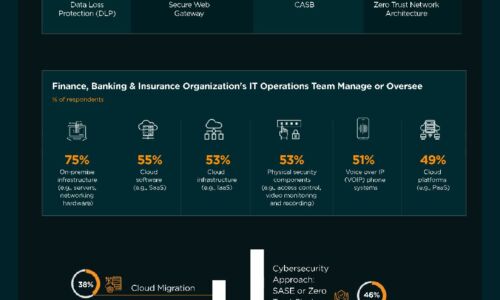
Finance, Banking & Insurance Industry | State of Cybersecurity 2021
This infographic by ISACA and HCL Technologies discusses the state of cybersecurity within the finance,...

Case Study - Malwarebytes Endpoint Protection and Response
Malwarebytes cut potential downtime to a matter of hours rather than weeks. Malwarebytes complements...

App Development as a Core Business Capability
Many organisations now understand the critical role that apps play in enabling their people, as well...

You've Got BEC!
A Roundup of the 10 Biggest, Boldest, and Most Brazen Business Email Compromise Scams of 2020 and 2019. It's...

10 Endpoint Security Problems Solved By The Cloud Infrographic
The three challenges you're likely facing – cost and complexity, defenses that can't keep up, and overburdened...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.




