Firewall

VP AppDev Confessions
Development teams burdened with complex release requirements often run over schedule and over budget....

Top 3 challenges your team faces when building in the cloud
Learn the root causes of the challenges your cloud and security teams are facing and see how these challenges...

Stay open for business — but closed to cyberthreats
E-commerce relies on always-on connectivity to customers whenever they want to access services. Your...
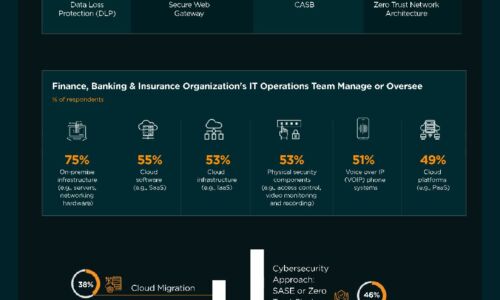
Finance, Banking & Insurance Industry | State of Cybersecurity 2021
This infographic by ISACA and HCL Technologies discusses the state of cybersecurity within the finance,...

KuppingerCole Leadership Compass
Leaders in innovation, product features, and market reach for access governance and intelligence. Delivering...

Delivering Fast and Secure Enterprise Applications
Adopting a zero trust security model — authenticating and authorizing every request, device, and user...

The Five Nastiest Security Mistakes Exposing Public Cloud Infrastructure
Public cloud infrastructure has become a critical asset to enterprises that compete on innovation. Protecting...

Data-Driven Transformation in Europe
Although governments across Europe may differ in their ideologies, statutes and constitution – there...

Don't Diverge—Converge
Digital acceleration is driving the adoption of hybrid IT architectures. These new hybrid environments...

IoT Use Cases: Smart Ports
Smart Ports utilize Internet of Things (IoT), Artificial Intelligence (AI), and data to make itself more...

The 4 Benefits of VPN Elimination
The corporate perimeter as you know it no longer exists. Virtual private network (VPN) vulnerabilities...

2021 State of the Threat in review
The State of the Threat report is compiled by the world-renowned Secureworks® Counter Threat Unit™...

Efficacy Of Micro-Segmentation Assessment Report
Micro-segmentation is an essential security control that prevents the lateral movement of attackers....
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.
