Endpoint Security
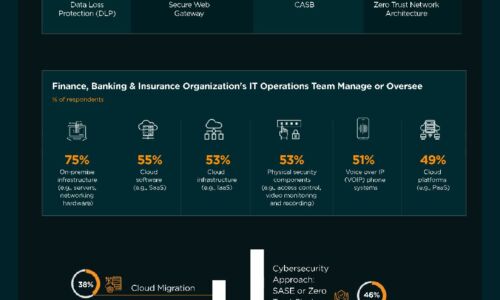
Finance, Banking & Insurance Industry | State of Cybersecurity 2021
This infographic by ISACA and HCL Technologies discusses the state of cybersecurity within the finance,...

The Total Economic Impact™ Of VMware Carbon Black Cloud
Security and IT teams today are constantly dealing with overly complex and siloed toolsets that can't...

Elastic Cloud Gateways: The Evolution of Secure Cloud Access
Enterprise security groups today face a daunting task. While their core responsibility of protecting...

Blurred Lines and Blind Spots Report
Of the many effects the COVID-19 pandemic has had on business, one of the most dramatic has been the...

State of Ransomware: Invest now or pay later
Ransomware attacks continue at a blistering pace because organizations remain vulnerable to the exploits...

Zero-trust Solutions for Comprehensive Visibility and Control
Zero-trust solutions exist for nearly every part of the network. However, a piecemeal approach can leave...

Why you need an adaptive security segmentation solution
The threat landscape is more dynamic than ever before, and as business-critical applications traverse...

Transforming the SOC: Building Tomorrow's Security Operations, Today
When you think of a security operations center (SOC), what comes to mind? Is it an organized team of...

Endpoint security versus productivity in utilities: a false choice?
Utility companies are often targeted because they can be used so effectively as phishing lures, as they...

Ransomware Prevention Is Possible
Ransomware is a form of malware that encrypts files to prevent victims from accessing their systems and...

Case Study - Malwarebytes Endpoint Protection and Response
Malwarebytes cut potential downtime to a matter of hours rather than weeks. Malwarebytes complements...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


