Endpoint Security

Filling the Gaps in Office 365
Office 365 offers a variety of choices and added functionality making it confusing for IT teams to decide...

Top 3 Challenges Your Team Faces When Building in the Cloud
Today's cloud and security teams are asked to do more with less. Although the capabilities and cost of...

Next-Gen Digital Transformation for Law Firms
Optimize opportunities to grow your practice and mitigate risk. Law firms, like other businesses, have...

Enable End-to-End Zero Trust To Achieve Effective Outcomes
Zero Trust priorities have evolved in 2020 to require solutions that secure your remote workforce with...

Securely Enabling a Hybrid Cloud in Microsoft Azure
The public cloud has rapidly moved past the novelty, curiosity stage to the business critical initiative...
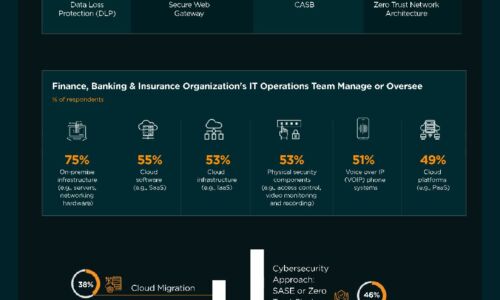
Finance, Banking & Insurance Industry | State of Cybersecurity 2021
This infographic by ISACA and HCL Technologies discusses the state of cybersecurity within the finance,...

Open Channels, Hidden Threats
How Communication and Social Media Tools Are Changing the Insider Risk Equation for Compliance, IT and...

Cybersecurity For Dummies
Advanced threats have changed the world of enterprise security and how organizations are attacked. These...

Which WAF is right for me eBook
Despite the tech industry's collective best efforts to bolster secure application development practices,...

Privileged Access and the Impact of Pass the Hash Attacks
The goal of this survey was to capture hard data on current experiences, trends and approaches to Identity...

Optimizing Workload Placement in Your Hybrid Cloud
Many IT organizations are in the process of modernizing their infrastructure, as part of either a digital...

BlackBerry Cyber Suite
The challenge of securing and protecting data and endpoints is not a new requirement, but today it is...

Incident Response Use Cases
According to an IBM study, the vast majority of organisations surveyed are unprepared to respond effectively...

Chart Industries vaporizes ransomware and malware
Malwarebytes enables IT to shift its focus to strategic security project work. The company in this case...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.