Email Security

Securing Microsoft 365 with Fortinet Security Fabric
The Fortinet Security Fabric provides broad, integrated, and automated protection across the organization—on-premises,...

The Future of Secure Communications
How BlackBerry's SecuSUITE is changing the way governments and enterprises communicate. In an increasingly...
Advanced Email Security
Email is a fundamental feature of modern business. Yet it is also the number one threat vector. Email...

7 Ways to Prevent Supply Chain Phishing Attacks
Your email and digital communications with suppliers, partners, vendors and other third parties represent...
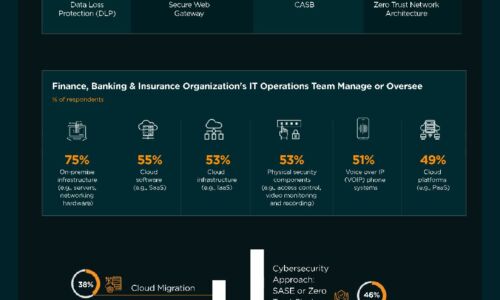
Finance, Banking & Insurance Industry | State of Cybersecurity 2021
This infographic by ISACA and HCL Technologies discusses the state of cybersecurity within the finance,...

The Total Economic Impact™ Of The CB Predictive Security Cloud
Your endpoints are one of the most targeted assets in your organisation. In 2017 alone, more than 50%...

Compromise Assessment Use Cases
With cyber attacks increasing both in quantity and sophistication, how can an organization know with...

Alphabet Soup: Making Sense of XDR, EDR, NDR, and SIEM
XDR, EDR, NDR, and SIEM. They are among the most prominent acronyms in cybersecurity. But what do they...

Part Four- Futureproofing your cybersecurity strategy
Email account takeovers are among the most insidious and damaging cyberattacks—used to invade companies...

Cybersecurity For Dummies
Advanced threats have changed the world of enterprise security and how organizations are attacked. These...

Use Case-Driven Cloud Security Evaluator Guide
Researching cloud security? Be sure you evaluate yourself and your vendors on the 6 most common cloud...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


