Email Security
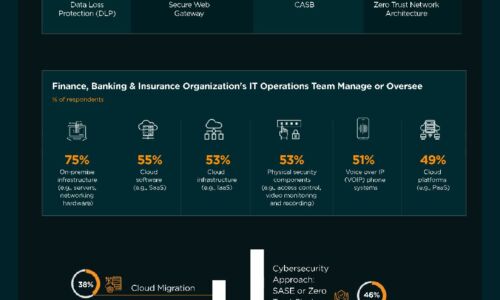
Finance, Banking & Insurance Industry | State of Cybersecurity 2021
This infographic by ISACA and HCL Technologies discusses the state of cybersecurity within the finance,...

How Malware Can Steal Your Data
As applications drive business, more and more valuable data is accessed and exchanged through them. Cybercriminals...

5 Reasons to Upgrade Your Symantec Email to Proofpoint
Symantec is now part of Broadcom, a semiconductor manufacturing company. For Symantec customers of all...

PhishBusters Survey: Perception vs. Reality of Phishing Attacks
Cofense conducted a survey to examine the general public's perceptions of phishing attacks, including...

Encryption, Privacy, and Data Protection: A Balancing Act
The Business, Privacy, and Security Mandates for Comprehensive SSL/TLS Inspection. Enterprise IT leaders...

Cyber Risk Commands C-suite's Focus: The State of Email Security 2023
As companies grow more skittish over rising economic volatility and intensifying geopolitical tensions,...

Case Study - Malwarebytes Endpoint Protection and Response
Malwarebytes cut potential downtime to a matter of hours rather than weeks. Malwarebytes complements...

Deploying Consistent Application Services in Multi-Cloud Environments
Most organizations prioritize cloud flexibility—and let application teams choose the best environment...

The Business Email Compromise Handbook
A Six-Step Plan for Stopping Payment Redirection, Supplier Invoicing Fraud and Gift Card Scams Sometimes,...

Ransomware Protection Checklist
Ransomware attackers are increasingly employing more sophisticated attacks and defeating existing defenses....

The Data Breach is Coming from Inside the House
Real-Life Tales of Data Loss, Insider Threats and User Compromise Data doesn't lose itself. People lose...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


