Cloud

14 innovative personalisation ideas for the digital-first customer
Prior to 2020, customer personalisation was a nice thought. However, the global pandemic shifted everything....
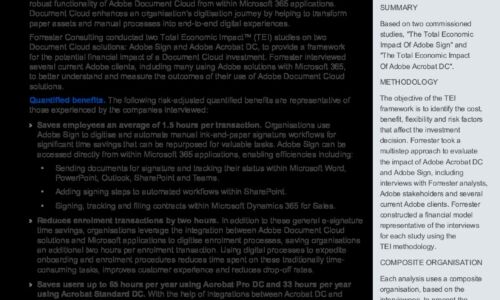
The Total Economic Impact of Adobe Document Cloud & Microsoft Spotlight
Forrester interviewed several current Adobe clients, including many using Adobe solutions with Microsoft...
The Characteristics of Your Future Technology Capabilities
Disruption -- whether big (COVID-19) or small (new start-up competitors) -- has more or less become commonplace...

Embrace Change: 4 Ways to Prepare for What's Next
Organizations large and small have been meeting the demand for hybrid work and learning environments,...

Office of the CTO Report: Continuous API Sprawl
APIs are a contract between the service provider and service consumer. When any application uses an API,...

How To Maximize Protection and Access, On Campus Or Off
Colleges and universities are increasingly dependent on cloudbased apps and mobile connectivity. Meanwhile,...

Employees are choosing how they work
'The measure of intelligence is the ability to change.' To remain connected, productive and secure in...

The Ultimate CX Agent Guide
Customers have embraced technology to manage all aspects of daily lives, setting off a digital disruption...

Cybercrime Tactics and Techniques - Attack on Home Base
The coronavirus pandemic has left the world looking very different at the end of the quarter than it...
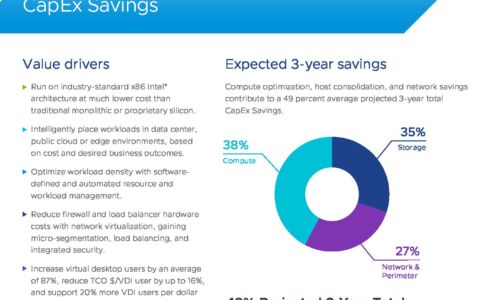
VMware Cloud Foundation: Maximise Digital Business Value
76% of IT organizations are committed to hybrid cloud as a long-term strategy to quickly adapt to changing...

An Overview of Insider Threat Management
As organistions move towards a more distributed workforce, the traditional perimeter of the office network...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


