AIM

Part One- Futureproofing your cybersecurity strategy
Ransomware is running amok. The term refers to a type of malware that encrypts the victim's data, preventing...

Securing high tech industry network data
We all understand the negative impact of data loss, so why is it that so many organisations seem to be...

The New Future of Work A Best Practice Guide for Manufacturing
For centuries, advances in technology have forced evolution in the way we live and do business. The fourth...
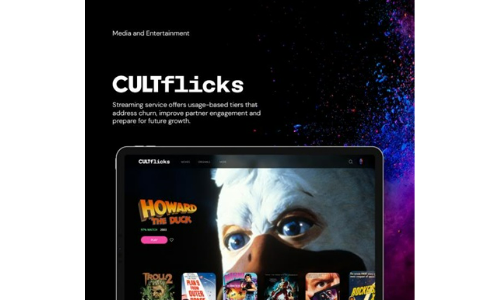
Cultflicks
CULTflicks is a niche video streaming entertainment company that offers the unique experience of specialized...

Finding a Setting Worthy of Your 'Crown Jewels'
Keep all the Data in a single, unified Database – Oracle Exadata For most companies, data is critical...

Making Employees Happier, More Productive, and Reassured
Companies have a responsibility to keep employees safe and maintain secure, functional workspaces that...

Zero-trust Solutions for Comprehensive Visibility and Control
Zero-trust solutions exist for nearly every part of the network. However, a piecemeal approach can leave...

Human Factor Report 2021
Cybersecurity, Ransomware and Email Fraud in a Year that Changed the World As the global pandemic upended...

Parivartana - The Role of Data and Analytics in Social Transformation
From personalized healthcare to digital farming, and from energy management to digital governance solutions,...

Report: An Executive's Guide to Industrial Cybersecurity
As enterprises invest heavily in digital transformation, industrial cybersecurity will increasingly serve...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.



